As defense contractors and manufacturers progress toward CMMC Level 2 compliance, a critical area of ambiguity lies in how Operational Technology (OT) is treated within the current Level 2 Scoping Guide. Specifically, the treatment of OT within the category of “specialized assets” leaves significant room for interpretation — and potential misalignment with the practical realities of OT risk management.
The Core Issue: “Unable to be Fully Secured”
The guide references “assets that can process, store, or transmit CUI but are unable to be fully secured,” which we believe is meant to account for systems that, due to technical limitations or business/operational constraints, cannot implement the full set of NIST SP 800-171 controls. However, this language lacks clarity — particularly around how “unable to be fully secured” is assessed, and by whom.
In practice, assessors with a traditional IT security background may interpret this phrase through the lens of what is technically possible, rather than what is operationally feasible and risk-appropriate in an OT environment.
This leads to the application of IT-centric expectations — such as enforcing MFA or endpoint protection — in environments where safety, availability, and deterministic behavior are critical, and where such controls may introduce unacceptable operational risk.
OT Risk Priorities: Safety and Availability First
OT systems are designed with fundamentally different priorities than IT systems. The OT security triad emphasizes:
- Safety – always prioritized before the CIA triad
- Availability – uptime and process continuity
- Integrity – accuracy and reliability of control data
- Confidentiality – often a secondary concern
This stands in contrast to NIST SP 800-171 and CMMC, where confidentiality of CUI is the focus.
A Better Approach: Proactively Define and Communicate OT Scope for CMMC Level 2
For organizations with OT environments, success in CMMC Level 2 assessments depends not just on technical control implementation, but on how clearly and proactively you define your scope and risk-based approach. Here’s how to do it effectively:
1. Categorize OT Assets as Specialized Assets
Begin by clearly identifying which OT systems fall under the Specialized Assets category, as defined in the Level 2 Scoping Guide. Justify their inclusion by documenting any constraints that limit implementation of certain NIST SP 800-171 controls — such as lack of vendor support, real-time processing needs, or operational safety considerations.
2. Document Risk-Based Security Policies
Make sure your security policies explicitly acknowledge that safety and availability are prioritized in your OT environment — and that this priority influences control selection and implementation. Reference the OT-specific CIA triad (Availability–Integrity–Confidentiality), and clarify how risk is assessed and mitigated in your environment.
3. Apply and Reference NIST SP 800-82 for Control Implementation
Use NIST SP 800-82 Rev. 2 as your technical guide for implementing controls in OT systems. Where controls from NIST SP 800-171 cannot be fully applied, document how equivalent protections are in place. For example:
- IA-2(2) (MFA): For OT systems that are not remotely accessible, NIST 800-82 recognizes that physical access controls can serve as one authentication factor.
- SI-3 and SI-4: Where malware protection agents cannot be installed, rely on network-level monitoring, whitelisting, and tight physical controls to detect and prevent malicious activity.
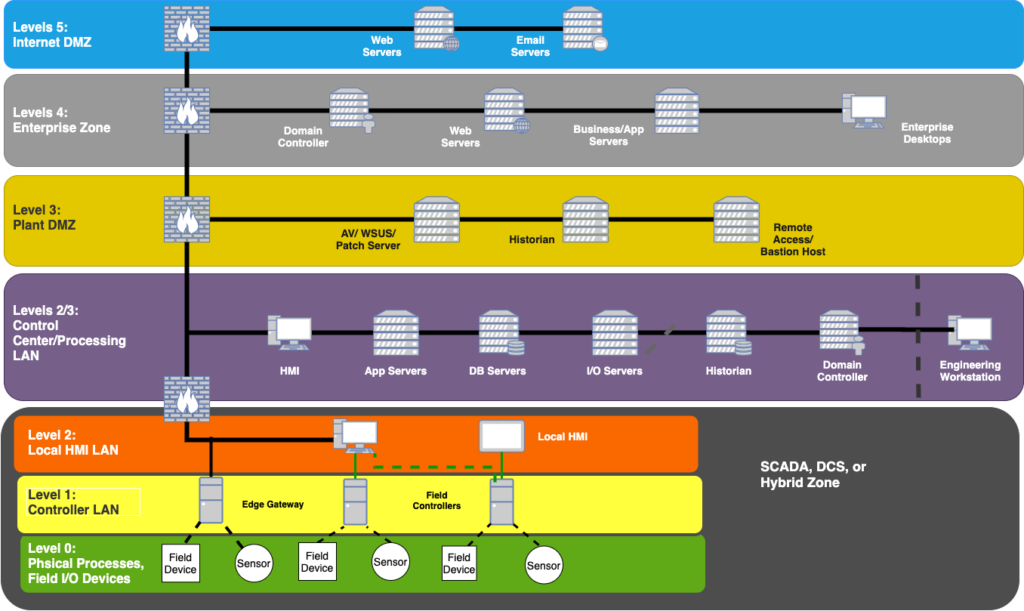
4. Segment Using the Purdue Model
Structure your OT environment according to the Purdue Enterprise Reference Architecture, ensuring lower-level OT devices (Levels 0–2) are logically and physically segmented from business networks (Levels 3–5). This not only aligns with best practices but helps bound the CMMC assessment scope in a defensible and auditable way.
5. Ensure an Assessor’s Understanding
Document all of the above and make it part of your pre-assessment briefing. Don’t assume your assessor has OT experience. Provide context on how your environment works, why standard IT controls may not be applicable, and how your compensating controls still meet the intent of the requirements.
Conclusion: Define OT Scope Early and Communicate Clearly
Organizations with OT systems must proactively define how these assets impact their CMMC assessment scope. Ensure your assessor understands:
- How OT assets are categorized as specialized assets
- That your organization has implemented a risk-based security model prioritizing safety and availability
- That controls have been implemented in alignment with NIST SP 800-82
Don’t assume your assessor will bring OT experience to the table — it’s critical to explain how control objectives are being met in a way that’s appropriate for your environment. By clearly documenting segmentation, compensating controls, and system limitations, you can align expectations early and avoid unnecessary friction during assessment.

